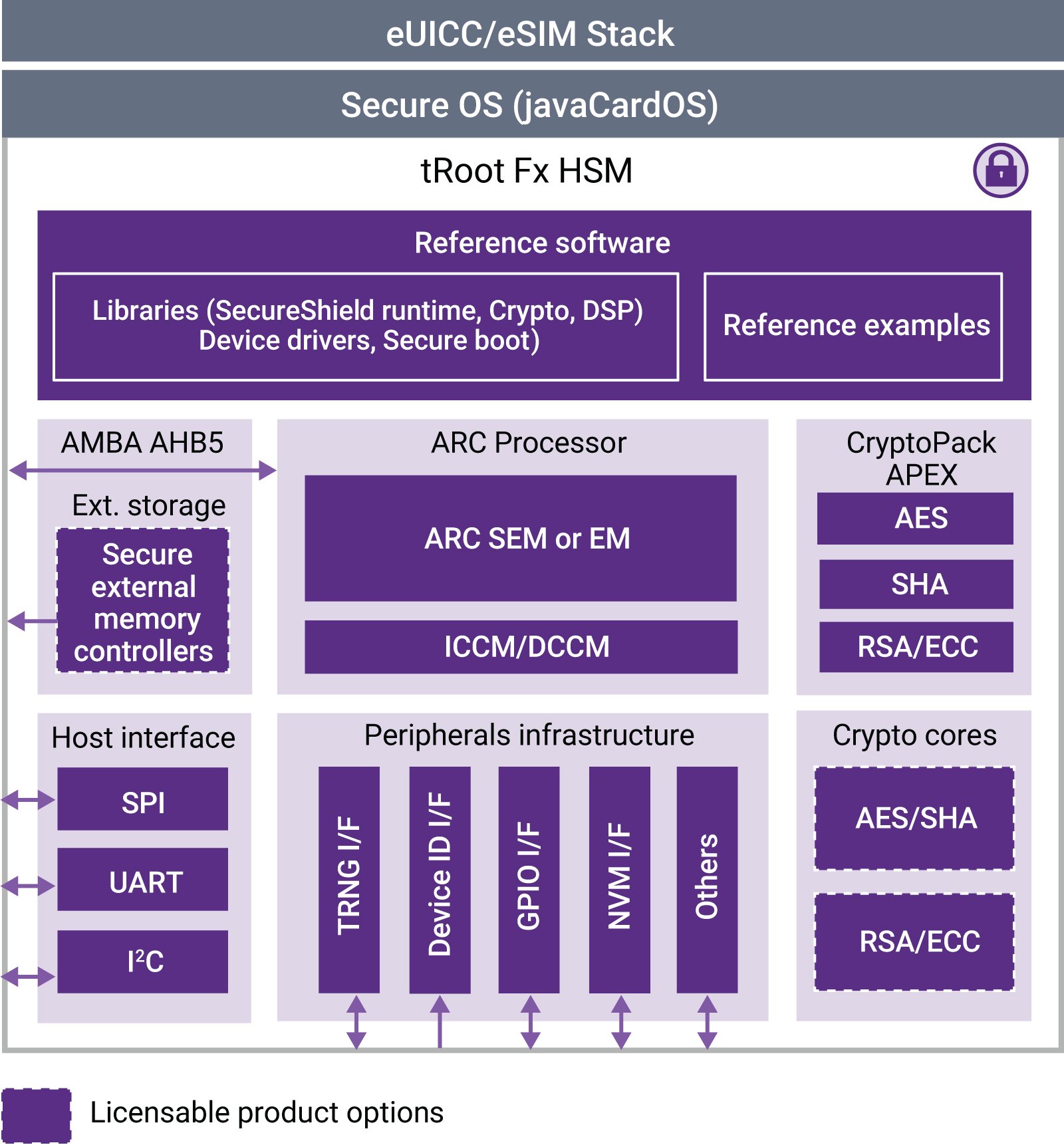
The Synopsys tRoot™ Fx Hardware Secure Modules (HSMs) are a flexible, highly configurable hardware and software solution that provides a programmable root of trust to secure high value embedded targets. It is designed for fast and easy integration within a larger system context.
The tRoot Hardware Secure Modules (HSMs) with Programmable Root of Trust enable connected devices to securely and uniquely identify and authenticate themselves to create secure channels for remote device management and service deployment. The flexible tRoot Fx HSM family includes fully programmable and highly configurable solutions that enable designers to tune the HSM to their exact requirements, while the pre-built tRoot Vx HSM family offers a defined security boundary for a complete, drop-in security solution. tRoot HSMs provide robust hardware-enforced protection while maintaining a high level of performance through cryptographic acceleration and offer designers options to create solutions with the most efficient combination of power, size and performance. tRoot HSMs provide a Trusted Execution Environment (TEE) to protect sensitive information and processing, and implement security-critical functions such as secure boot, storage, debug, anti-tampering and key management required throughout the device life cycle.
Highlights & Key Features
- Pre-verified subsystem protects against malicious attacks targeting high value applications
- Protects against side-channel attacks
- Software and hardware cryptography options accelerate a range of crypto algorithms including AES, 3DES, SHA-256 and RSA/ECC
- Secure instruction and data controllers provide external memory encryption and authentication
- Software includes NIST-validated platform libraries cryptography library, secure boot toolkit, and SecureShield runtime library
- Choice of energy-efficient ARC SEM110, SEM120D, EM4 + ESP, or EM5D + ESP processors
- Extensive collection of hardware accelerated cryptography options
- Secure instruction and data memory controllers
- Host and peripheral interfaces (UART, NVM, GPIO, TRNG, Device ID)
- Included software offers:
- NIST-verified cryptography library
- Small-footprint drivers for all I/O
- DSP functions supporting signal processing (SEM120D)
- Secure boot software
- ARC SecureShield runtime library
Product Details
Find Your IP
Search for IP
Quickly identify and access the right IP solutions for your project needs.
Foundation IP Selector
Find embedded memory and logic IP for your SoC design.
Non-Volatile Memory IP Selector
Find silicon-proven NVM IP for your SoC design needs.






