Antifuse-Based Split-Channel 1T-Fuse Bit Cell for OTP NVM IP
At the heart of all Synopsys One-Time Programmable (OTP) Non-Volatile Memory (NVM) IP is the memory array, using a patented, area-efficient, antifuse bit cell – 1T‑Fuse – that employs gate-oxide breakdown as a robust, non-reversible programming mechanism. This is a proven, reliable and secure technology that has been widely adopted and used in a broad range of applications and markets.
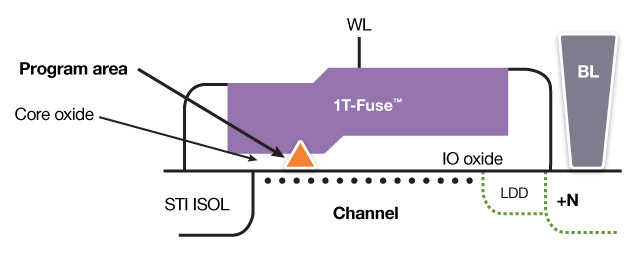
The single-transistor OTP bit-cell (1T-Fuse) uses a unique split-channel architecture, where a single transistor gate covers both I/O (thick) and core (thin) oxides. The cell is programmed by a controlled, irreversible breakdown from the gate through the core (gate) oxide to the channel. The bit cell is programmed either with an embedded charge pump or through an external pin (at the tester, for example). The bit-cell is implemented using standard CMOS processes and requires no additional mask steps.
Arrays are available from a few 100 bits to around 1M bit and may be cascaded for even larger macros. Synopsys memory arrays are very flexible and can replace multi-time programmable memory in many applications. Conversion to mask ROM is also simple.
Available in standard CMOS processes, Synopsys OTP memory arrays don’t require additional mask layers or process steps and provide a viable alternative to mask ROM, eFuses and Flash memory. The reduced size of the single-transistor bit cell results in better yield, higher security, improved reliability and lower overall cost.
Security Features
The inherent security features of the 1T-Fuse bit-cell include:
- Programming is by permanent structural change in few atomic layers (located far from diffusion)
- No physical attack can reveal programmed state in FinFET or HKMG technologies
- No leakage in non-programmed state
- State cannot be changed through exposure to high temperature, voltage or radiation
- No charge or voltage involved in state retention (unlike floating gate NVM, e.g. flash)
- State of memory (even for a few bits) is virtually impossible to detect using physical attack or reverse engineering techniques